
While HIPAA’s general concepts are relatively well understood, putting them into practice is much more complex. The transition to digital healthcare presents many challenges to handling protected health information (PHI), determining whether a company is a covered entity, and ensuring that PHI use is compliant. Keeping up with changing regulations and technologies can be difficult, so our team at Itirra has compiled this guide to help you handle PHI from creation to deletion.
What is Protected Health Information (PHI)?
The proliferation of healthcare technology has made it more challenging to determine what constitutes PHI. Consumers are sharing more and more health information with companies that operate very differently from traditional health organizations.
The HIPAA Privacy Rule defines protected health information as “individually identifiable health information” that covers an individual’s past, present, or future health conditions. It also details administration of healthcare and the payments associated with that care. Some examples of this are test results, patient records, and insurance information.
What is a Protected Health Information (PHI) Identifier?
HIPAA outlines 18 identifiers that constitute PHI because they can be used to identify an individual. Unless permitted by HIPAA or with patient consent, any identifiers should not be disclosed.
However, due to the age of this list, affected companies should ensure that there are no other identifiers before disclosing health information to third parties, such as for research purposes. In addition to the content of the list, affected companies should protect information such as social media usernames and other digital identifiers.
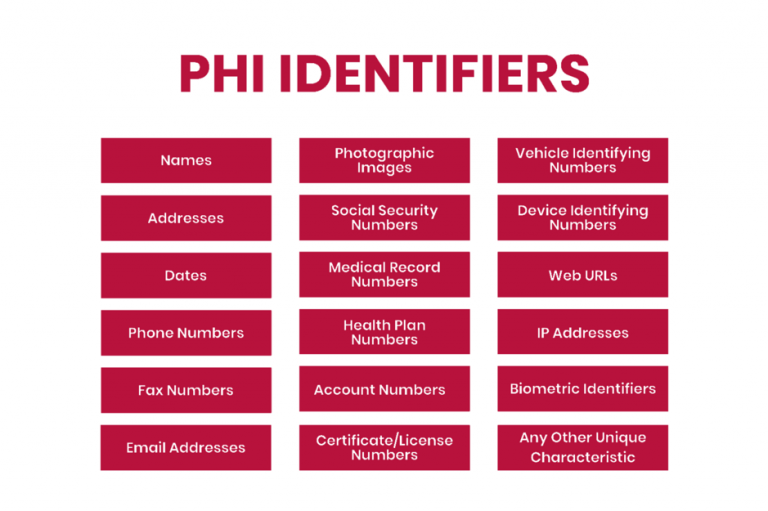
Exceptions to the PHI Definition
Not all medical records qualify as protected health information under HIPAA as various exceptions exist that depend on who collects health information: a person, company, or service. Although confusing because they often contain personally identifiable information, the following categories are exceptions to HIPAA’s definition of PHI:
Education Records: items such as allergies or disabilities in education records are not considered PHI.
Employment Records: similar to education records, employment records are not considered PHI, and the OHSA statement is listed as an exception to the disclosure law.
Data from portable devices: if a company that makes the device and collects the data stores the information, it’s not PHI. It becomes PHI when shared with a healthcare organization or used to administer healthcare.
Let’s break down the portable devices exception. Fitness trackers, wearables, and mobile device apps can track health information, such as heart rate, blood pressure, and oxygen levels, that would constitute PHI under the Affordable Care Act (ACA). Although the app technically provides healthcare services, HIPAA does not apply. If the app developer is not a Covered Entity (CE) or a Business Associate (BA), data collected and stored by the app is not considered PHI. Instead, it is considered consumer health information or personal health information, which is not required to comply with HIPAA.
The example above changes if the app developer works with a doctor or a hospital. If they direct patients to use the app to enhance healthcare services, then the app developer would be considered a BA under HIPAA. The data collected and stored by the device would be regarded as PHI and would need to be HIPAA-compliant.
When unsure whether the information is PHI, it’s better to treat it with the same care as any other medical data. Playing it safe is the only way to protect your business from potential legal action in the case of an unauthorized disclosure or breach.
What is ePHI?
Electronic Protected Health Information (ePHI) is any health-related information created and stored electronically. Quite simply, it’s digital PHI. The HIPAA Security Rule provides specific guidance on monitoring ePHI, meaning companies that collect and store electronically protected health information must comply with HIPAA.
Are subcontractors responsible for PHI security?
BAs of BAs are known as subcontractors. When subcontractors have access to PHI, they must sign a Business Associate Agreement (BAA) with the business partner they are working with. A cloud service provider such as AWS is the most common example of a subcontractor. If PHI is stored in the cloud, companies using the cloud must sign a BAA with the service provider.
Most cloud service providers have standardized responsibility-sharing agreements. In this case, the company providing the cloud service is responsible for securing the cloud itself, while the company using the cloud provider is responsible for its security. If your company is a Covered Entity, make sure your business partner has subcontracted the BAA. If your company is the BA of the affected entity, it’s best to ensure that each subcontractor signs a BAA.
What are the best practices for handling PHI?
Storing and accessing PHI
The HIPAA security rule requires CEs and BAs to implement administrative, physical, and technical safeguards for all physical or digital PHI. These requirements must be followed to achieve HIPAA compliance and handle PHI, as they are critical to preventing breaches and protecting patient privacy. Below are some of the required security controls included in the HIPAA Security Rule.
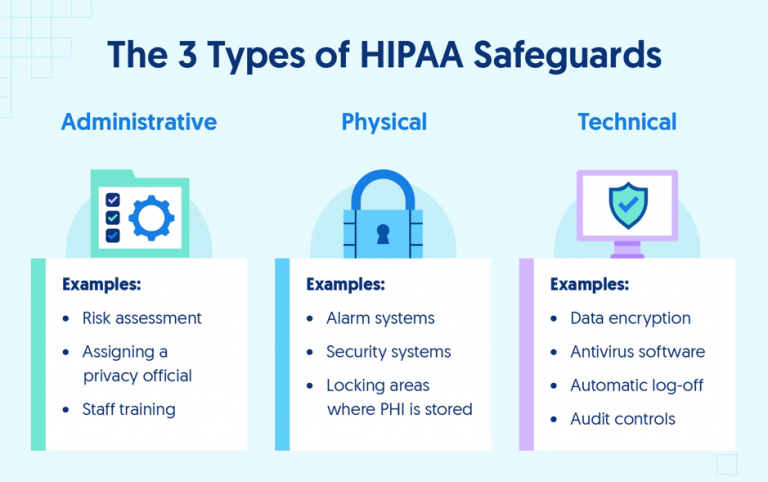
Administrative Safeguards of the HIPAA Security Rule
Administrative control is mainly policy-centered. In any organization, all employees who have access to computer systems should complete security awareness training with specific HIPAA training for different departments. Organizations should also conduct risk assessments to identify and remediate potential vulnerabilities.
Any access, transfer, or modification of PHI should be logged for possible audits. HIPAA requires security policy logs and changes to security systems to be kept for six years after their last use.
Physical Safeguards of the HIPAA Security Rule
With PHI becoming increasingly digital, it is essential to have adequate physical safeguards, including security systems in facilities handling PHI, locked filing cabinets for paper PHI, restricted access to workspaces with PHI, and other barriers to entry into areas where protected information is stored.
For many healthcare companies, physical security safeguards primarily focus on equipment and device security. For example, organizations need to be able to remotely wipe any device containing PHI if it’s lost or stolen to be HIPAA-compliant. Any physical or digital location with PHI backups should have all necessary controls to keep the data secure. Internal risk assessment is one way to discover vulnerabilities, while audits are a more thorough option to secure systems.
Technical Safeguards of the HIPAA Security Rule
Technical safeguards are a vital part of PHI security because many healthcare providers host their data in the cloud. Good network and device security are crucial for preventing security breaches. Organizations using a third-party cloud service must ensure that their services handle PHI correctly. AWS, Microsoft Azure, and Google Cloud all allow using their services in a HIPAA-compliant manner.
Companies that host on their servers must have a strong network firewall installed and record the status of the firewall. All employees should have secure passwords and use multi-factor authentication to log into systems with PHI. Another technical safeguard is secure transmissions because secure storage is useless if data can’t be sent securely.
How to de-identify PHI?
Covered Entities and Business Associates must only protect data classified as PHI, which means that health data that cannot be used to identify an individual does not need to be protected. De-identification is a method of anonymizing PHI so it can be handled freely post-transformation. Once data is anonymized, you no longer need to worry about HIPAA compliance when handling that data.
There are mainly two methods of anonymization: safe harbor and expert judgment.
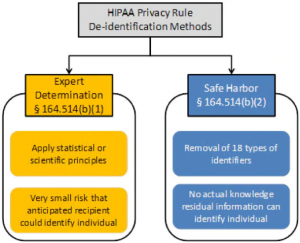
Safe Harbor method of PHI de-identification
The Safe Harbor method removes PHI identifiers from the records. The 18 identifiers include names, addresses, and other information outlined at the beginning of the article. After data has been anonymized, the next step is to go through the data to confirm that it’s impossible to re-identify individuals using the data.
If de-identification is not successful following the removal of the identifiers, it is necessary to omit certain records entirely when using the Safe Harbor method. For example, suppose you’re conducting a study on how different jobs affect blood pressure. If only one or two judges are in the sample, their records should be deleted. The small sample size can result in an increased likelihood of re-identification. As a result, there should not be a way to link health data back to individuals.
Expert Determination method of PHI de-identification
The Expert Determination method of de-identification of PHI requires the HIPAA Covered Entity or Business Associate to obtain the opinion of a qualified statistical professional that the risk of re-identifying individuals from the data set is very low. In such cases, the method used to determine and justify the expert opinion must be documented and retained by the CE or BA and made available to the supervisory authority in case of an audit or investigation.
When applying these methods and principles, experts must conclude that the risk of an individual being re-identified is minimal and must remain low when the data is combined with other information reasonably available to the intended recipient. HIPAA doesn’t define the risk of re-identification, only stating that it should be “very small” to the context of the data set, the specific circumstances, and the ability of the intended recipient to re-identify the individual.
How to disclose and transfer PHI?
PHI Disclosure Guidelines is an essential part of HIPAA that governs the rules for disclosure of PHI. Covered Entities can disclose PHI with the patient’s permission, but the rules for disclosure without permission are more complex.
Mandatory Disclosures of PHI
HIPAA also mandates disclosure under certain circumstances. Some examples are preventing the spread of infectious diseases, situations involving suspected child or elder abuse, and compliance with court orders.
Permissive Disclosures of PHI
The most important reasons for disclosing PHI are treatment, payment, and healthcare activities, including scenarios where healthcare professionals use PHI to determine how best to treat patients or to review previous treatments. PHI can be used to bill patients or their insurance providers. You may also disclose PHI to relevant third parties if the third parties have a relationship with the patient and the disclosure is for the purposes described above.
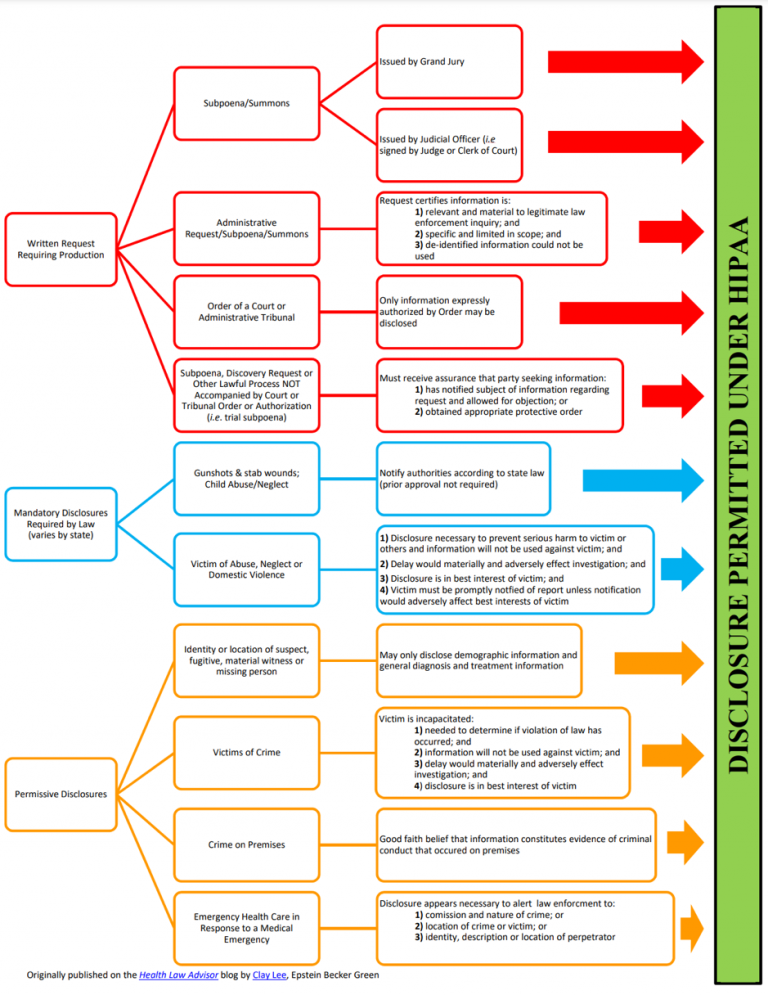
Sending and receiving PHI
Another essential precaution to protect patient privacy is only to transmit PHI using secure methods. The methods you use should be HIPAA compliant, avoiding text messages, emails, and other unencrypted forms of communication. Many CEs use patient portals that are already HIPAA compliant.
PHI access and retention
A vital part of the Privacy Rule is the right it gives individuals to receive a copy of their PHI. CEs have 30 days to respond to patients’ written requests for copies of so-called designated medical records. A designated medical record that contains enrollment records, test results, billing documents, and official medical advice is there to help doctors make health care decisions. Patients have the right to have inaccuracies corrected in their designed medical records.
HIPAA also requires organizations to keep logs of privacy policy notices, employee training, data recovery plans, and more. The Privacy Rule includes different data retention requirements, whereby companies should retain information relevant to their compliance activities, including policies, procedures, and risk assessments.
Conclusion
HIPAA has significant implications for PHI in the healthcare industry, but by staying compliant with software security standards, healthcare providers can reduce internal and external threats to their health-sensitive data. However, lack of encryption, insecure communication channels, and inconsistent access controls are common problems with medical software. Even something as trivial as a push notification can result in a HIPAA violation, and developing secure and HIPAA-compliant software is always a challenge.
At Itirra, we know how to create secure software for healthcare businesses that need it. Our team has extensive experience building comprehensive healthcare solutions. Contact us today to learn how to achieve and maintain HIPAA compliance while developing software for your business.
