
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. law that provides privacy and security regulations to protect medical information. The law has become increasingly important in recent years as cyber and ransomware attacks on health insurers and providers have led to numerous health data breaches.
The federal law was signed into law by President Bill Clinton on August 21, 1996. HIPAA takes precedence over state laws regarding the security of medical information unless state laws are deemed stricter than HIPAA.
What are the five main sections of HIPAA?
HIPAA has five sections or headings:
Title I - HIPAA Health Insurance Reform
Title I protects health insurance coverage for people who change or lose jobs and prohibits group health plans from refusing coverage to people with certain medical and pre-existing conditions and from setting lifetime coverage limits.
Title II - HIPAA Administrative Simplification
Title II instructs the U.S. Department of Health and Human Services (HHS) to develop national standards for processing electronic health transactions. In addition, healthcare organizations must implement secure electronic access to medical records and comply with privacy regulations established by HHS. In the healthcare world, most professionals refer to HIPAA Title II compliance when they say HIPAA compliance.
Title III - HIPAA Tax-Related Health Provisions
Title III contains tax regulations and guidelines for health care.
Title IV - Application and Enforcement of Group Health Plan Requirements
Title IV further clarifies the health insurance reform, including provisions for those with pre-existing conditions and those seeking continued coverage.
Title V - Revenue Offsets
Title V contains provisions regarding proprietary life insurance and the treatment of persons who have lost their American citizenship for income tax purposes.
The HHS Office for Civil Rights (OCR), or the HIPAA enforcer, conducts audits and issues fines for non-compliance with HIPAA. Violating HIPAA has proven to be very costly for healthcare organizations.
What is the purpose of HIPAA?
Healthcare organizations must comply with Title II. It states that affected companies must take reasonable and appropriate security measures to protect patient data. Some of these assurances must include administrative measures. These measures include staff training and risk analysis, including physical protection measures and safeguards like access controls, technology deployments, and cybersecurity software.
In general, Title II states that organizations must ensure the availability, confidentiality, and integrity of all patient information. Businesses also need to protect themselves from anticipated security threats. Additionally, they must prevent the inappropriate use and disclosure of patient information. HIPAA laws require healthcare providers to ensure compliance in the workplace.
At the same time, it does not prescribe any specific measures. In this regard, the law provides some flexibility. Here, organizations are free to choose how to comply with HIPAA guidelines. However, the flexibility creates ambiguity, and figuring out how to meet HIPAA standards can be difficult.
What are HIPAA-covered businesses?
HIPAA only applies to Covered Entities and their Business Associates (BAs). A HIPAA Covered Entity is any organization directly handling protected health information (PHI) or personal health records (PHRs). Affected companies must comply with HIPAA and Health Information Technology for Economic and Clinical Health (HITECH) legislation to protect PHI and PHR.
There are three categories of Covered Entities:
Healthcare providers – include doctors, clinics, psychologists, dentists, chiropractors, nursing homes, and pharmacies.
Health plans – include health maintenance organizations (HMOs), company health plans, health insurance companies, and government healthcare programs: military healthcare programs, Medicare, and Medicaid.
Healthcare clearinghouses – entities that process non-standard health information received from another entity into a standard format, and vice versa. Examples include billing services and municipal health systems for managing health data.
Businesses can use this HHS decision tool to determine if they qualify as a HIPAA Covered Entity or BA and, therefore, must comply with HIPAA.
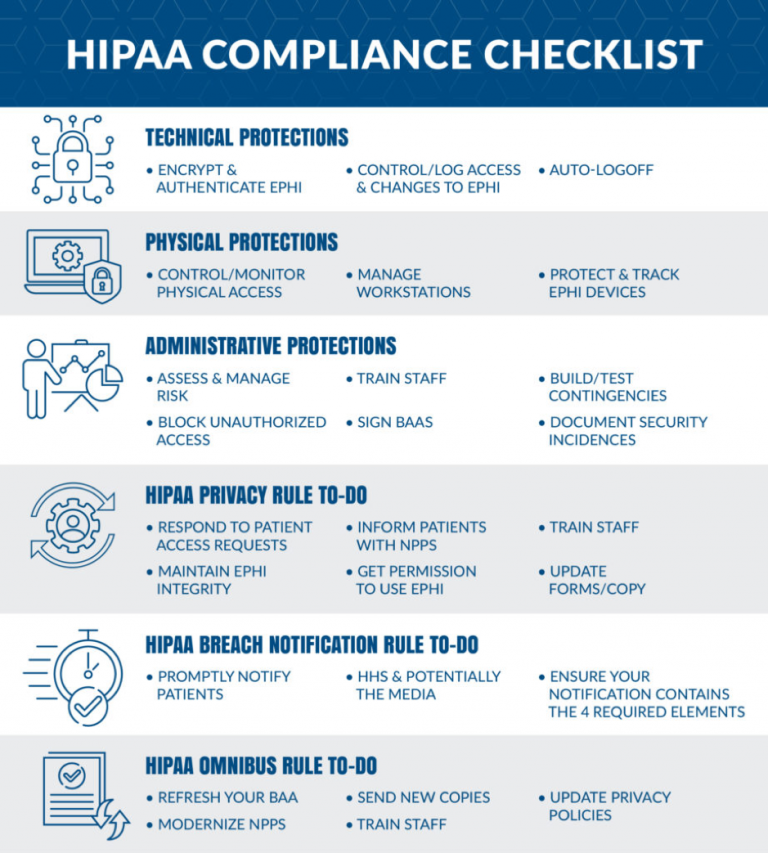
What are the main principles of HIPAA?
Privacy Rule (45 CFR §164.530)
Privacy rules protect an individual’s PHI and medical records, with limitations and conditions on uses and disclosures that can and cannot be made without the patient’s consent. The HIPAA Privacy Standard pertains to the same legislation as the HIPAA Privacy Rule, a specific standard within the HIPAA law that focuses on protecting PHI.
The Privacy Rule establishes national standards for how affected companies, healthcare clearinghouses, and business partners share and store PHI. These are rules in place to protect patient information used during medical care.
The HIPAA Privacy Standard governs the following:
Patients’ right to access their PHI
Healthcare providers’ right to access patient PHI
Healthcare providers’ right to deny access to patient PHI
The Privacy Rule also ensures that patients have the right to examine, obtain a copy of their records, and request that their records be corrected. Patients can submit the following forms, which affected entities need to respond to as dictated by the Privacy Rule:
Request for Accounting Disclosures form
Notice of Privacy Practices (NPP) form
Authorization for Use or Disclosure form
Request of Access to Protected Health Information (PHI)
Request for Restriction of Patient Health Care Information
Privacy Complaint Form
Security Rule (45 CFR §164.308)
The Security Standards for the Protection of Electronic Protected Health Information, often called the HIPAA Security Rule, establishes national standards for protecting patient information stored or transmitted electronically. It is based on the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
The Security Rule defines and governs the standards, methods, and procedures for protecting electronic PHI during storage, accessibility, and transmission. The rule covers hardware, software, and transmission risk analysis and risk management protocols. There are three levels of security protection:
Administrative security arrangements address the allocation of HIPAA security compliance teams
Technical safeguards involve encryption and authentication methods used to control access to data
Physical safeguards include securing any electronic systems, data, or equipment in your facility and organization
OCR enforces the HIPAA safety rule, which seeks to balance patient safety with the advancement of health technology. The regulation requires the installation of physical and electronic safeguards to ensure the secure transfer, maintenance, and receipt of PHI. When resolving the risks and vulnerabilities associated with PHI, healthcare organizations should ask three key risk analysis questions:
Can the source of PHI within the organization be identified — including any PHI created, received, maintained, or transmitted?
Are there external sources of PHI, and what are they?
What are the natural, human, and environmental threats to information systems containing PHI?
The answers to these questions can help organizations decide what actions they need to take to plan, develop, and maintain a HIPAA-compliant security management process, such as:
Set up personnel screening
Determine which data to back up
Determine how and where data is backed up
Determine how, where, and when to use encryption
Determine what data should be verified for data integrity
Implement access controls on physical workstations and electronic media and data
Transactions Rule
This rule addresses transactions and code sets used in HIPAA transactions, including ICD-9, ICD-10, HCPCS, CPT-3, CPT-4, and NDC codes. Covered entities and BAs must use the standards correctly to ensure the security, accuracy, and confidentiality of medical records and PHI. Under HIPAA, the electronic exchange of healthcare data must be in the form set out by HHS, including:
Payment and remittance advice
Claims status
Eligibility
Coordination of benefits
Claims and encounter information
Enrollment and disenrollment
Referrals and authorizations
Premium payments
HIPAA-covered entities who conduct any of these transactions electronically must use an adopted standard from ASC X12N or NCPDP (for certain pharmacy transactions).
Identifiers Rule
HIPAA provides various identifiers for affected entities using HIPAA for financial and administrative transactions. HIPAA requires healthcare providers to have a National Provider Identifier (NPI) number to identify them in their administrative transactions. HIPAA uses three unique identifiers for affected entities using HIPAA-regulated administrative and financial transactions. These identifiers are:
National Provider Identifier (NPI) – a 10-digit number used for covered health care providers in each HIPAA administrative and financial transaction
National Health Initiative Identifier (NHI), used as a part of the Centers for Medicaid Services (CMS), is an identifier used to identify health plans and payers
Standard Unique Employer Identifier – identifies an employer entity in HIPAA transactions and is deemed the same as a state Employer Identification Number (EIN)
Enforcement Rule
The HIPAA enforcement rules address penalties for non-compliance by business associates or covered entities in the following five areas:
HIPAA privacy and security rules compliance
Mandatory reporting requirements for security breaches compliance
Accounting disclosure requirements compliance
Marketing and sales restrictions compliance
Restrictions applicable to contracts with BAs or covered entities must be in place before PHI can be transferred or shared.
This Enforcement Rule is derived from the ARRA HITECH ACT and expanded under HIPAA Privacy and Security with increased penalties for violations.
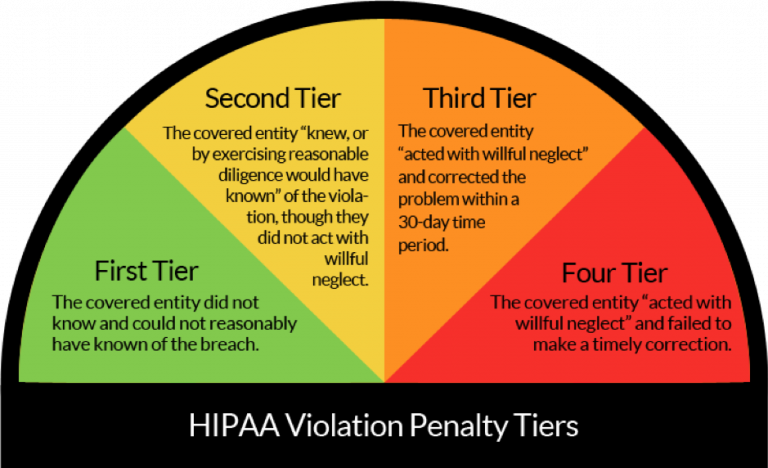
Breach Reporting Rule
The HIPAA Breach Notification Rule sets national standards to be followed when a data breach compromises patient data. The rule also addresses two other types of violations. Other violations are divided into minor and major violations. All business partners and affected companies must report all PHI breaches, regardless of size, to HHS. The exact reporting procedure depends on the type of violation.
Conclusion
HIPAA has significant implications for the healthcare industry, but by staying compliant with software security standards, healthcare providers can reduce internal and external threats to their health-sensitive data. However, lack of encryption, insecure communication channels, and inconsistent access controls are common problems with medical software. Even something as trivial as a push notification can result in a HIPAA violation, and developing secure and HIPAA-compliant software is always a challenge.
At Itirra, we know how to create secure software for healthcare businesses that need it. Our team has extensive experience building comprehensive healthcare solutions. Contact us today to learn how to achieve and maintain HIPAA compliance while developing software for your business.

