
For most healthcare organizations, protecting patient information is the most critical and challenging aspect of HIPAA. Protected Health Information (PHI) under HIPAA refers to protected data, but the concept is similar to the term personally identifiable information (PII) used in other compliance regulations.
Even though PII and PHI are alike, they are not interchangeable. Understanding how they intersect is essential in ensuring data security and HIPAA compliance. Healthcare organizations that recognize the complexities of both may save money, time, and hassle while protecting customers and patients from harm.
What is Personally Identifiable Information (PII)?
The National Institute of Standards and Technology (NIST) defines Personally Identifiable Information (PII) as data that includes any information directly or indirectly associated with an individual’s identity. The definition has nothing to do with HIPAA and is not regulated by any entity or industry like PHI.
In the past, personal data consisted only of social security numbers, phone numbers, postal addresses, or email addresses. However, as technology and software advance, the scope of PII continues to expand. PII may now include login IDs, digital images, IP addresses, social media posts, and other data in digital form.
Name, such as full name, alias, maiden name, mother‘s maiden name, etc.
Personal identification numbers, such as social security number (SSN), driver‘s license number, passport number, bank account number, taxpayer identification number, or credit card number
Address information, such as home address or billing address
Email address and online login IDs
Personal characteristics, such as photos of faces or identifying features, handwriting, fingerprints, and biometrics (voice signature, retina scan, or facial geometry)
Any information linked or linkable to previous points, such as race, date of birth, place of birth, weight, activities, religion, geographical indicators, employment information, medical information, education information, and financial information.
PII must be kept safe and confidential because it can result in a high degree of risk and potential harm should it be leaked, lost, or stolen. To that end, NIST created guidelines to help organizations properly manage and protect PII, where they describe Confidentiality Impact Levels – a scale that identifies the potential harm an individual may experience if PII is accessed, used, or disclosed in an unauthorized manner.
The Confidentiality Impact Levels are determined by assessing the potential harm to individuals and organizations if PII falls into the wrong hands, starting from limited adverse effects for those whose information is lost. Adverse effects are negative physical, social, or financial consequences that may occur to the holder of the information or the organization responsible for the breach

What is Protected Health Information (PHI)?
Protected health information is a subcategory of PII, but it specifically pertains to health information shared with Covered Entities (CEs) under HIPAA. Medical records, lab reports, hospital bills, and any information related to an individual’s past, current, or future physical or mental health is PHI. It also describes the administration of healthcare and related payments. Examples include test results, medical records, and insurance information.
The HIPAA Privacy Rule provides federal protections for PHI handled by covered entities and gives patients rights to that information. At the same time, the Privacy Rule allows the disclosure of personal health information needed for urgent patient care, emergencies, and other vital purposes.
HIPAA Privacy Rule categorizes covered entities into health plans, healthcare clearinghouses, healthcare providers, and hybrid entities such as universities with hospitals and academic medical centers. Suppose a covered entity contracts a Business Associate (BA) that can process PHI. In that case, the company must have a Business Associate Agreement (BAA) that requires its employees to comply with HIPAA standards.
HIPAA outlines 18 identifiers in the PHI that can identify an individual. No identifiers should be disclosed except as permitted by HIPAA or with patient consent. However, covered entities should ensure that no other identifiers exist before disclosing health information to third parties. In addition to the list’s contents, affected companies should protect information such as social media usernames and other digital identifiers.
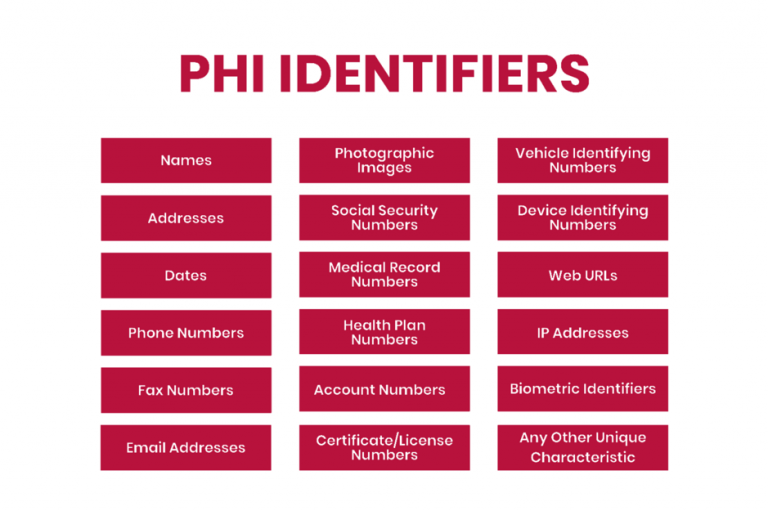
To separate PHI from its HIPAA protections for research and other purposes, organizations can anonymize health data by removing all 18 PHI identifiers. Once data can no longer be traced back to an individual, it is no longer PHI and is not protected by HIPAA.
PHI regulations aim to protect patient privacy and allow providers to facilitate care coordination. Rather than being a barrier to care or preventing information sharing entirely, the HIPAA Privacy Rule ensures that PHI is shared only with patient consent or for care coordination between affected entities.
Home addresses and phone numbers are not PHI by themselves, but if these data points are combined with health conditions, treatment plans, or other specific health information, they change from PII to PHI. Identifiable health information is not deemed PHI unless the organization is a HIPAA-covered entity.
What happens if a PII or PHI breach occurs?
Businesses handling PII need to consider how many people could be affected by a data breach, how easy it is to link PII to a specific individual, where the data is stored, and who has access to it.
PII that has a high level of impact on some people may have a low level of impact on others. Every organization has different needs depending on what personal data they store and how it is organized. For example, social security numbers are more sensitive than phone numbers, so that they can be classified as high sensitivity. Additionally, a breach involving ten people is likely to have a more negligible impact than a breach affecting 100,000, which could influence how companies assess risk.
When a PII breach occurs, organizations must report the incident. However, data breach notification laws vary by state, and some experts believe companies are too lax in notifying the public and governments.
HIPAA also has specific rules for notifying violations. As part of HIPAA compliance best practices, organizations must notify anyone whose data has been compromised within 60 days of a data breach. To help minimize the chances of a breach, companies must encrypt PHI, and the encrypted information is exempt from security breach notifications unless the key is also made public. In many cases, this can mean the difference between a decision to close and a costly breach report.
In addition, affected companies must send written notice to all affected individuals by mail and post a notice on their website home page for at least 90 days. Specific requirements vary by state.
PHI breaches adhere strictly to the HIPAA Security Rule, which sets national standards for protecting the electronic personal health information of individuals created, received, used, or maintained by covered entities or business associates. The rule also requires healthcare organizations to implement data security measures to ensure data confidentiality.
How to secure PII and PHI?
The methods for protecting PII and PHI are mostly the same. No matter what type of sensitive information a company holds, it’s critical to keep systems up to date and apply strict cybersecurity standards.
The best technological safeguards for PII involve companies implementing robust cybersecurity protocols and strict control over digital access. NIST recommends installing antivirus software, keeping computers patched, and prohibiting the use of personal devices on an organization’s network. It’s also essential to educate employees on common phishing tactics and cyber hygiene habits to avoid compromising the company network.
HIPAA goes beyond recommended PII safeguards in its requirements for covered entities and business associate relationships. Healthcare providers have significant legal liability under the HIPAA Privacy Rule for violations caused by their business associates.
Covered entities have strict obligations to protect PHI where patient safety is at stake. Patients trust their healthcare providers to protect them by providing life-saving surgery, preventive care, and emergency services. But HIPAA also requires providers and health care plans to protect sensitive patient information.
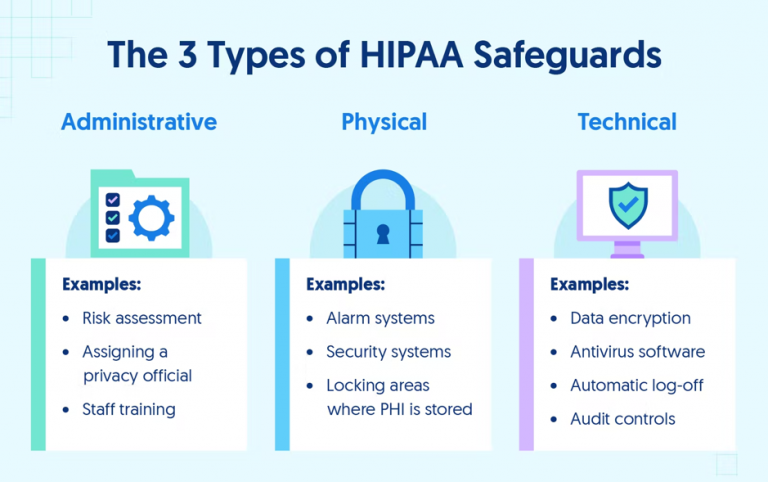
The HIPAA Security Rule requires CEs and BAs to implement administrative, physical, and technical safeguards for all physical or digital PHI. These requirements must be followed to achieve HIPAA compliance and handle PHI, as they are critical to preventing breaches and protecting patient privacy. Below are some of the required security controls included in the HIPAA Security Rule.
Conclusion
Following PII security best practices helps organizations stay secure. HIPAA isn’t a set of arbitrary rules to make life miserable for healthcare companies — it’s a valuable framework for ensuring high standards of care and patient confidentiality. The best approach to PII is to simplify compliance by turning it into a single comprehensive set of rules that can be used across the whole organization, maximizing patient safety and ensuring that sensitive information is secure.
PII and PHI have significant implications for companies that interact with consumer data, but by staying compliant with software security standards, they can reduce internal and external threats to their data. However, lack of encryption, insecure communication channels, and inconsistent access controls are common problems with medical software. Even something as trivial as a push notification can result in a HIPAA violation, and developing secure and HIPAA-compliant software is always a challenge.
At Itirra, we know how to create secure software for healthcare businesses that need it. Our team has extensive experience building comprehensive healthcare solutions. Contact us today to learn how to achieve and maintain HIPAA compliance while developing software for your business.
