
In today’s rapidly evolving healthcare landscape, the protection of sensitive patient data is of paramount importance. The Health Insurance Portability and Accountability Act (HIPAA) sets stringent guidelines for safeguarding the privacy and security of patient health information (PHI). As healthcare organizations increasingly rely on digital systems and software solutions to manage PHI, ensuring HIPAA compliance is vital for maintaining patient trust and preventing costly data breaches.
Developing software solutions that adhere to HIPAA regulations not only protects patient data but also enables healthcare providers to deliver better care and improve outcomes. As the industry continues to embrace digital transformation, it is crucial for healthcare organizations to invest in secure, HIPAA-compliant technologies that uphold the highest standards of patient privacy.
By understanding the intricacies of HIPAA regulations and leveraging modern technologies such as Fast Healthcare Interoperability Resources (FHIR) and Health Level Seven International (HL7) standards, organizations can create a robust foundation for secure, interoperable healthcare systems. Join us as we delve into the world of HIPAA compliance, exploring the best practices for developing secure healthcare software solutions that effectively protect PHI and ensure seamless data exchange across multiple systems.
A wealth of experience in healthcare software development and a deep understanding of HIPAA compliance makes Itirra a trusted partner for healthcare organizations seeking to build secure, interoperable HIPAA-compliant solutions. Our team of experts is well-versed in the latest technologies and industry standards, including FHIR and HL7, ensuring that the solutions we create not only meet regulatory requirements but also drive efficiency, improve patient outcomes, and build a solid foundation for future growth in the healthcare sector
Understanding HIPAA regulations
HIPAA is a crucial piece of legislation that governs the handling of PHI in the United States. With the rise of digital health technologies and the increasing use of standards like FHIR and HL7 for data exchange, it is imperative that healthcare organizations and software developers have a deep understanding of HIPAA regulations to ensure compliance and maintain patient privacy.
Privacy Rule
The Privacy Rule establishes national standards for protecting individuals’ PHI, which includes any information that can be used to identify a patient and is created, received, stored, or transmitted by a healthcare organization. It sets forth the conditions under which PHI may be used or disclosed by covered entities, such as healthcare providers, health plans, and clearinghouses, and their business associates. The Privacy Rule also grants patients the right to access and request corrections to their PHI.
Security Rule
The Security Rule focuses on safeguarding electronic PHI (ePHI) by outlining the administrative, physical, and technical safeguards that covered entities and their business associates must implement. These safeguards are designed to protect the confidentiality, integrity, and availability of ePHI. Healthcare software developers must take these requirements into account when designing and building their solutions, incorporating features like encryption, access control, and auditing mechanisms to ensure compliance.
Breach Notification Rule
The Breach Notification Rule mandates that covered entities and their business associates notify affected individuals, the Department of Health and Human Services (HHS), and in some cases, the media, in the event of a breach of unsecured PHI. Timely notification is crucial for mitigating the potential harm caused by a breach and maintaining trust between patients and healthcare providers.
Developing HIPAA-compliant healthcare software solutions requires a thorough understanding of these regulations and the ability to apply them effectively in a rapidly evolving technological landscape. This not only helps organizations avoid costly penalties and reputational damage but also fosters a culture of trust and confidence among patients and stakeholders.

Assessing risk and identifying requirements
Before developing HIPAA-compliant software solutions, healthcare organizations and their software development partners need to conduct a comprehensive risk assessment and identify the specific requirements necessary to achieve compliance. This involves evaluating potential vulnerabilities and threats to PHI and taking into account the latest advancements in data exchange technologies, such as FHIR and HL7. This section will cover the essential steps in assessing risk and identifying requirements to create secure and compliant healthcare software solutions.
Conducting a risk assessment
A thorough risk assessment is a crucial starting point for ensuring HIPAA compliance. It involves identifying all the ePHI within an organization and evaluating the potential risks and vulnerabilities associated with its storage, transmission, and processing. This assessment should include both internal and external threats, such as unauthorized access, data breaches, and natural disasters.
Organizations should document their findings, implement appropriate safeguards, and regularly review and update their risk assessments to address new and evolving threats. Based on the risk assessment, organizations should identify the specific requirements necessary for HIPAA compliance in their software solutions. This includes considering aspects such as access controls, encryption, and data storage.
Access controls
Implement strong access control mechanisms to restrict unauthorized access to ePHI. This may include unique user identification, authentication procedures, and role-based access controls to ensure that only authorized personnel can access sensitive information.
Encryption
Incorporate encryption technologies to protect ePHI during transmission and at rest. This helps prevent unauthorized access and ensures the integrity of sensitive data, even in the event of a breach.
Data storage
Ensure that ePHI is securely stored, whether on-premises or in the cloud. Implement backup and disaster recovery plans to safeguard against data loss and ensure the availability of critical systems in case of emergencies.
By conducting a thorough risk assessment and identifying the requirements for HIPAA compliance, healthcare organizations can work with experienced partners like Itirra to develop software solutions that adequately protect patient data while leveraging the latest advancements in FHIR, HL7, and other key technologies.
Designing and implementing HIPAA-compliant solutions
Developing HIPAA-compliant software solutions involves incorporating a range of best practices to ensure the security and privacy of PHI. These strategies not only help organizations meet regulatory requirements but also contribute to improved patient care and outcomes.
FHIR and SMART on FHIR are pivotal in driving healthcare interoperability, a crucial factor in enhancing patient care, streamlining operations, and fostering innovation within the industry. By embracing these groundbreaking technologies, healthcare organizations can unlock the true potential of digital health and deliver better, more connected, and patient-centric care. Seamless, secure, and efficient exchange of health information is at the heart of this transformation, which offers numerous benefits for healthcare providers, patients, and the industry as a whole:
Incorporate privacy by design
Adopt a privacy-by-design approach during the development process, integrating privacy and security measures into the software’s architecture from the outset. This proactive approach helps identify and address potential vulnerabilities before they become issues, ensuring that PHI is protected throughout the system’s lifecycle.
Implement strong authentication and authorization
Use robust authentication and authorization mechanisms to ensure that only authorized users have access to ePHI. Multi-factor authentication (MFA) can provide an additional layer of security by requiring users to provide multiple forms of identification before granting access to sensitive data.
Secure data transmission
Secure the transmission of ePHI by implementing industry-standard encryption protocols such as TLS (Transport Layer Security). This ensures that data remains confidential and protected from unauthorized access during transit between systems.
Employ data minimization techniques
Limit the collection, use, and retention of PHI to only what is necessary for the intended purpose. By minimizing the amount of sensitive data stored and processed, healthcare organizations can reduce their risk exposure and enhance patient privacy.
Regularly monitor and audit system activity
Implement continuous monitoring and auditing processes to detect and respond to potential security incidents quickly. This involves tracking user activity, logging system events, and conducting periodic security audits to ensure ongoing compliance with HIPAA requirements.
Develop and maintain a robust incident response plan
Establish a comprehensive incident response plan to address potential security breaches and minimize their impact. This plan should outline the roles and responsibilities of team members, the steps to be taken in the event of a breach, and procedures for notifying affected individuals and regulatory authorities as required by the HIPAA Breach Notification Rule.
Incorporate the latest technologies and standards
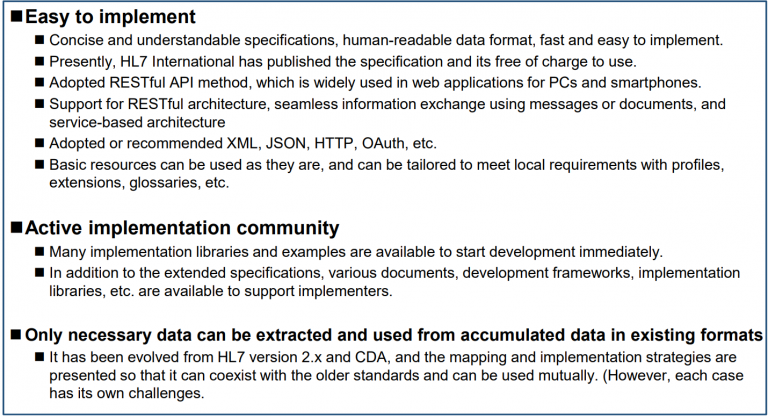
Embrace modern technologies and industry standards, such as HL7 FHIR, to facilitate seamless and secure data exchange between various healthcare systems. By implementing these advanced standards, healthcare organizations can ensure their software solutions are not only HIPAA-compliant but also interoperable, future-proof, and capable of adapting to the ever-evolving healthcare landscape.
Testing, validation, and maintenance
Ensuring HIPAA compliance in healthcare software solution development goes beyond the initial design and implementation. Rigorous testing, validation, and ongoing maintenance are essential to maintaining the integrity and security of these systems.
Rigorous testing
The development of HIPAA-compliant solutions requires thorough testing to validate that the implemented security measures and data handling practices are effective in safeguarding PHI. This includes functional testing, penetration testing, and vulnerability assessments to identify and address potential weaknesses in the system.
Validation
In addition to testing, healthcare software solutions must undergo a comprehensive validation process to ensure they adhere to HIPAA regulations and any other applicable industry standards, such as HL7 and FHIR. This validation process helps to confirm that the system meets all regulatory requirements and can effectively protect patient data.
Continuous maintenance and monitoring
HIPAA compliance is not a one-time achievement; it requires ongoing efforts to maintain the integrity and security of healthcare software solutions. Regular system updates, security patches, and periodic audits are crucial to addressing new threats and vulnerabilities as they emerge. Additionally, continuous monitoring helps identify and resolve any potential compliance issues before they escalate, ensuring the long-term protection of PHI.
Partnering with HIPAA development experts
Navigating the complex landscape of HIPAA regulations and implementing secure healthcare software solutions can be challenging for healthcare organizations. Partnering with experienced HIPAA development experts, can provide invaluable support and guidance throughout the process. What are the benefits of collaborating with seasoned development partners and what advantages do they bring to the table?
Expertise in regulatory compliance
HIPAA development experts possess extensive knowledge of the regulatory landscape, including the Privacy Rule, Security Rule, and Breach Notification Rule. They can help healthcare organizations navigate these complex regulations, ensuring that software solutions are designed and implemented with full compliance in mind.
Experience with industry standards
Development partners like Itirra are well-versed in industry standards, such as HL7 and FHIR, which are crucial for enabling seamless data exchange and interoperability between healthcare systems. By incorporating these standards into software solutions, organizations can facilitate efficient and secure data sharing across various healthcare entities.
Best practices in security
HIPAA development experts have a deep understanding of best practices in data security and privacy. They can help healthcare organizations implement robust security measures, such as access controls, encryption, and secure data storage, to protect PHI and maintain compliance.
Conclusion
Developing HIPAA-compliant solutions is a critical aspect of modern healthcare software development, as it ensures the protection of sensitive patient information and fosters trust between healthcare providers and patients. By understanding the nuances of HIPAA regulations, conducting thorough risk assessments, implementing secure design practices, and maintaining continuous monitoring and validation processes, healthcare organizations can successfully develop and deploy secure software solutions that comply with the stringent HIPAA requirements.
As a leading Seattle-based healthcare software development company, Itirra has extensive expertise and experience in developing HIPAA-compliant solutions. By partnering with Itirra, healthcare organizations can efficiently navigate the complex landscape of healthcare data security and privacy, leveraging the latest technologies and industry standards to ensure full compliance and deliver exceptional patient care.
