
IIn an era where data breaches are a frequent headline and healthcare organizations are handling increasingly large volumes of sensitive data, protecting Protected Health Information (PHI) has never been more critical. Regulatory standards such as HIPAA, and data exchange protocols like FHIR and HL7, have been established to ensure the secure handling of healthcare data. However, as we navigate the intricate realm of healthcare security, there is a need for a more comprehensive, all-encompassing approach to ensure the safety of patient information.
As a recognized security framework, HITRUST integrates and harmonizes numerous recognized standards and regulatory requirements, creating a singular, unified approach to ensure healthcare data security. As we peel back the layers of HITRUST, we discover its invaluable role in healthcare data security, risk management, and regulatory compliance.
Here at Itirra, a leading Seattle-based healthcare software development company specializing in secure, HITRUST-compliant solutions, we aim to illuminate the role of HITRUST, its benefits, and how healthcare organizations can implement this benchmark standard in their operations.
What is HITRUST? Understanding the basics
HITRUST, or the Health Information Trust Alliance, was created to establish a comprehensive security framework that addresses the multitude of regulatory standards and best practices in the industry. In the realm of healthcare data security, HITRUST stands as a landmark standard that many healthcare organizations aspire to achieve.
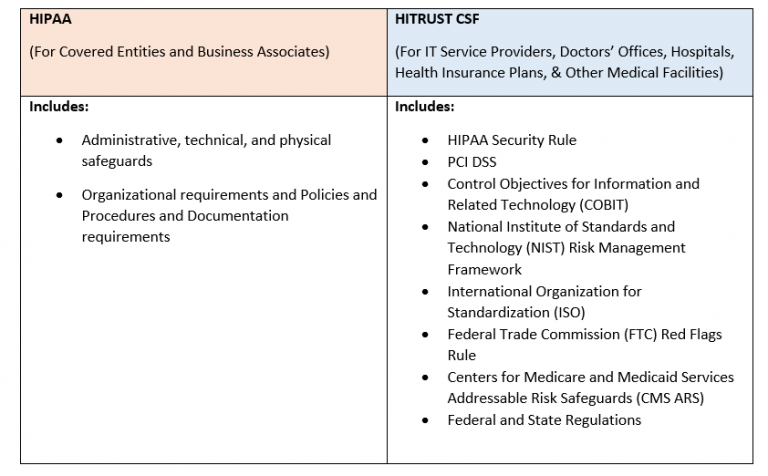
At its core, HITRUST is a certification that signals a healthcare organization’s commitment to protecting sensitive patient data. To achieve this certification, healthcare entities must demonstrate their adherence to the stringent controls set forth in the HITRUST Common Security Framework (CSF). This framework encompasses various regulatory standards and guidelines, including HIPAA, NIST, ISO, and more.
In simpler terms, HITRUST is essentially a gold standard in healthcare data security, providing an industry-approved benchmark for risk management and compliance. It brings together various standards and regulations under one umbrella, simplifying the complex landscape of healthcare data security and providing an organized, consolidated pathway for organizations to ensure their data protection efforts meet the highest standards.
Developed and maintained by IT, privacy, and information security professionals, the HITRUST CSF offers a unified, risk-based approach to data protection. It’s robust controls and flexible adoption levels make it suitable for organizations of all sizes and scopes. Whether you’re a small clinic just starting your digital transformation journey or a large hospital with advanced IT systems, understanding and adopting HITRUST can pave the way for better data security, enhanced trust with patients and partners, and improved regulatory compliance.

What are the components of the HITRUST framework?
The HITRUST Common Security Framework is a rigorously designed system that addresses the numerous regulations and standards in the healthcare industry. It stands as the centerpiece of the HITRUST approach, integrating multiple frameworks into one holistic structure. Let’s explore the main components of the HITRUST CSF for a clearer understanding of its composition and operation.
Regulatory and standards integration
HITRUST CSF is a harmonized set of controls that brings together many existing security standards and regulations, including HIPAA/HITECH, ISO 27001, NIST SP 800-53, PCI DSS, and more. This integration significantly simplifies the task of maintaining compliance with multiple requirements, providing a unified, consolidated set of controls.
Scalability and flexibility
The HITRUST CSF is designed to adapt to organizations of varying sizes, types, and complexity levels. It offers scalability and tailoring options based on specific organizational, system, or regulatory factors. As such, businesses can adopt the HITRUST framework that aligns best with their unique needs and risk environments.
Risk-based approach
The HITRUST CSF follows a risk-based approach to information security. It allows for the implementation of controls based on the specific risk factors an organization faces. This targeted, risk-oriented perspective makes the framework highly effective in addressing real-world data protection challenges.
Certification and assurance programs
HITRUST certification offers a clear demonstration of an organization’s commitment to data security and compliance. It also provides third-party assurance programs that enable businesses to verify their compliance levels and highlight areas for improvement.
Continuous updates and evolution
The HITRUST CSF is not static. It continually evolves to address emerging threats, regulatory changes, and technological advancements. This dynamic nature ensures that HITRUST remains relevant and effective in the ever-changing landscape of healthcare data security.
The importance of HITRUST in healthcare
In the healthcare industry, data is more than just numbers and facts. It’s a lifeblood that fuels the smooth operation of hospitals, clinics, and medical centers around the globe. Yet, as critical as data is in healthcare, it also presents a massive responsibility. Protecting sensitive healthcare information is paramount.
HITRUST is not just about complying with a set of rules. It represents a commitment to patient privacy, data security, and the integrity of healthcare systems. It is about ensuring that the sensitive data at the core of healthcare services is kept safe from breaches and cyber threats. It reassures patients that their private medical information is in good hands.
But the significance of HITRUST extends beyond just the immediate realm of data security. Adherence to the HITRUST framework can bring about operational benefits as well. It can lead to a more efficient audit process and more streamlined risk management. By following the standards outlined by HITRUST, healthcare providers are taking steps towards better overall governance.
Healthcare organizations must strive to stay ahead of potential cyber threats. It is a continuous, proactive effort that involves every aspect of an organization. In this context, HITRUST serves as a beacon, guiding healthcare organizations in safeguarding their patient data while conforming to the highest standards of security and compliance.
The landscape of healthcare data security is an ever-changing one, and HITRUST is instrumental in helping healthcare organizations navigate it. By building a solid foundation of trust and security, healthcare organizations can focus on their ultimate goal: providing the best possible care for their patients.
At Itirra, we understand the critical role that HITRUST plays in the healthcare industry. Our commitment to data security and privacy aligns with the HITRUST framework, ensuring our clients’ data is secure and their operations are compliant. By understanding and implementing HITRUST standards, we contribute to a safer and more secure healthcare ecosystem where patient data protection is a top priority. Our expertise enables us to provide solutions that not only meet HITRUST standards but also add value to the healthcare services our clients provide.
Achieving and maintaining HITRUST certification
Securing HITRUST certification is a rigorous and comprehensive process, but one that provides substantial benefits in the form of robust data security and regulatory compliance. But how does a healthcare organization go about achieving and maintaining this coveted certification? The following steps outline the typical path toward HITRUST certification:
Gap analysis
The initial step in the certification process involves carrying out a gap analysis. In this stage, organizations scrutinize their existing information protection programs and identify areas where they do not meet HITRUST requirements. These could include shortcomings in data encryption, data access controls, risk management procedures, or employee training programs, among others. The objective is to provide an understanding of where the vulnerabilities lie and what needs to be improved to comply with HITRUST standards.
Remediation
Once the gaps have been identified, the next step is remediation. This phase involves implementing the necessary controls to fill the gaps identified in the first stage. These actions can be varied, such as refining certain policies to better protect patient data, deploying new technology solutions that offer enhanced data security, or educating staff on data handling best practices to minimize human error-induced breaches.
Assessment
After the remediation phase, the implementation of the controls is assessed to ensure they meet HITRUST’s requirements. This process is usually conducted by an external HITRUST assessor. It involves a thorough evaluation of the implemented controls, ensuring they function as intended and effectively manage risk in line with the HITRUST CSF. This might involve on-site audits, interviews, and the examination of supporting documentation.
Validation and certification
If the assessment stage is successful, the organization can then move onto the validation and certification stage. The assessor prepares a validation report which is then submitted to HITRUST for a quality assurance review. If everything is in order, HITRUST issues the CSF certification. But, it’s important to note that certification isn’t permanent; it’s valid for two years, and an annual self-assessment is recommended to ensure ongoing compliance.
Continual monitoring
Achieving HITRUST certification is not the end of the journey. It’s vital for healthcare organizations to continuously monitor their controls and make adjustments as necessary. Regular internal audits, staff training refreshers, and staying abreast of evolving regulatory requirements can all play a part in ensuring the organization maintains its certification and continues to uphold the highest standards of data protection.
Achieving and maintaining HITRUST certification is a demanding yet crucially important process for any healthcare organization. It not only attests to an organization’s commitment to data security but also assures patients and partners that their sensitive information is handled with the utmost care and integrity.
Conclusion
Understanding and implementing the HITRUST framework is an indispensable aspect of data security in today’s healthcare landscape. As we’ve explored in this article, HITRUST provides a comprehensive and flexible approach to securing PHI. It enables healthcare organizations to demonstrate their commitment to security, privacy, and regulatory compliance. The journey to HITRUST certification may be arduous, but the benefits, ranging from enhanced trust with patients and partners to improved risk management, make it an investment worth considering.
As healthcare continues to evolve in the age of digital transformation, the value of robust, reliable data security measures will only increase. HITRUST certification serves as a beacon of trust in a complex and fast-paced industry, assuring all stakeholders that an organization is committed to maintaining the highest standards of data protection. For any organization navigating the complexities of the healthcare industry, understanding HITRUST isn’t just a recommendation – it’s a necessity.
If you’re looking for HITRUST compliant healthcare software solutions that prioritize the safety and integrity of patient data while offering innovative features, we’re here to assist you. Don’t navigate the complex world of healthcare data security alone. Reach out to Itirra today, and let us help you on your journey towards HITRUST certification and beyond. After all, we believe that robust security should never compromise on functionality or patient care.
